02-vcenter服务部署¶
理论知识¶
Vcenter一般指 VMware vCenter™ Server
VMware vCenterServer 提供了一个可伸缩、可扩展的平台,为 虚拟化管理奠定了基础。 VMware vCenter Server(以前称为 VMware VirtualCenter),可集中管理 VMware vSphere 环境,与其他管理平台相比,极大地提高了 IT 管理员对虚拟环境的控制。
VMware vCenter Server:提高在虚拟基础架构每个级别上的集中控制和可见性,通过主动管理发挥 vSphere 潜能,是一个具有广泛合作伙伴体系支持的可伸缩、可扩展平台。
在各个级别提供集中控制能力和可见性
无论您拥有几十个虚拟机,还是几千个虚拟机,VMware vCenter Server 都是管理 VMware vSphere 最简单、最有效的方法。 借助 VMware vCenter Server,可从单个控制台统一管理数据中心的所有主机和虚拟机,该控制台聚合了集群、主机和虚拟机的性能监控功能。 VMware vCenter Server 使管理员能够从一个位置深入了解虚拟基础架构的集群、主机、虚拟机、存储、客户操作系统和其他关键组件等所有信息。
借助 VMware vCenter Server,虚拟化环境变得更易于管理,一个管理员就能管理 100 个以上的工作负载,在管理物理基础架构方面的工作效率比通常情况提高了一倍。
主动管理 VMware vSphere
动态数据中心环境要求使用主动管理,利用标准化和自动化来最有效地利用 VMware vSphere 的灵活性。 利用简化和标准化的工作流将业务要求与 IT 流程连接起来,帮助消除代价高昂的错误并降低对手动任务的依赖。
VMware vCenter Server 可让管理员使用标准化模板迅速部署虚拟机和主机,并利用自动修正确保与 vSphere 主机配置以及主机和虚拟机补丁程序级别的遵从性。 VMware vCenter Server 还可让管理员控制关键功能,例如 vSphere VMotion、 Distributed Resource Scheduler、 High Availability 和 Fault Tolerance。 强大的编排引擎使管理员能够创建和轻松实施最佳实践工作流。
借助主动管理,VMware vCenter Server 允许您通过动态调配新服务、分配资源和自动化高可用性服务来满足业务要求和提高服务级别。
可扩展的管理平台
当将虚拟化扩展到整个数据中心时,您希望您的管理平台即能扩展以适应组织需要,又能嵌入现有体系结构中。 借助 VMware vCenter Server,您可以有效管理大型企业,并且具备通过一个控制台管理 1,000 多个主机和最多 10,000 个虚拟机的能力。
此外,VMware vCenter Server 的开放式插件体系结构可支持来自 VMware 及其合作伙伴的各种附加功能。 超过 300 个 VMware 合作伙伴直接与 vCenter Server 集成,这使您可以轻松地扩展平台,从而在多个方面实现更先进的管理功能,例如容量管理、遵从性管理、业务连续性和存储监控等。 vCenter Server API 还允许客户集成物理管理工具和虚拟管理工具,通过使用他们选择的企业管理工具连接到 vCenter Server。
软件获取¶
百度云下载地址链接: https://pan.baidu.com/s/1wUrPbvfV-o1lWDtGYQJBsQ 密码: k062
准备环境¶
首先准备一台能够通esxi管理网的windows跳板机,并登录跳板机
安装部署¶
接着进入镜像,进行vcenter机器的安装

进入镜像中,找到install的可执行文件——》双击启动,

点击安装

点击继续

选择我同意

选择第一个

这里是输入esxi的信息

选择yes

这是我们创建的vcenter的机器,虚机名和root密码——》默认的root用户密码是“V123.”

接着选择虚机的规格,因为是本地的虚机,所以就是最小化的了,

选择磁盘,

这里设置vcenter的机器的IP,

这里是配置都完事了,显示下所有的信息,

接着就开始部署了 ,等着吧!

现在我们的vcenter虚机就安装完成了,可以查看到,访问的页面是——》5480端口,
初始化配置¶
PS:这里不要点击continue,不要,不要!

接着我们再打开一个浏览器页面,访问下vcenter的地址,注意这里是https!!!

登录之后选择设置,

这里的密码是——》V123.

选择下一步

系统名称这里我们选择和IP地址相同,

接着设置SSO域名,然后设置vcenter页面登录的密码——》Uplooking!23

选择同意然后点击下一步

点击完成

接着等待安装就好了,

纳管ESXI¶
当我们vcenter机器创建好之后,就可以将esxi也纳管进入的,新建对应的数据中心,

接着新建集群,

然后添加主机,

输入ip账户密码

完成纳管

虚拟机开机自启动¶

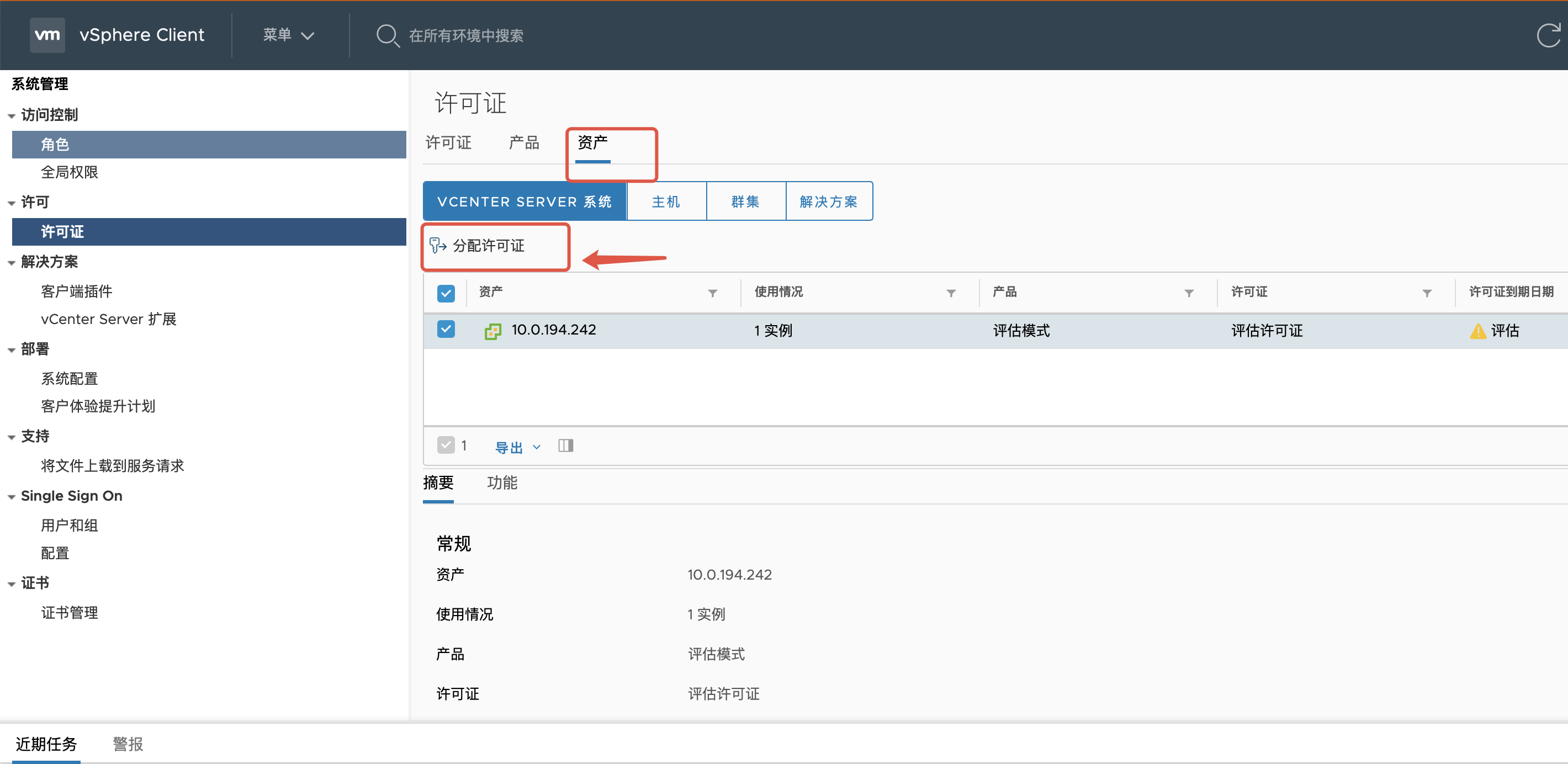
激活许可证¶
系统管理》vcenter server设置》许可
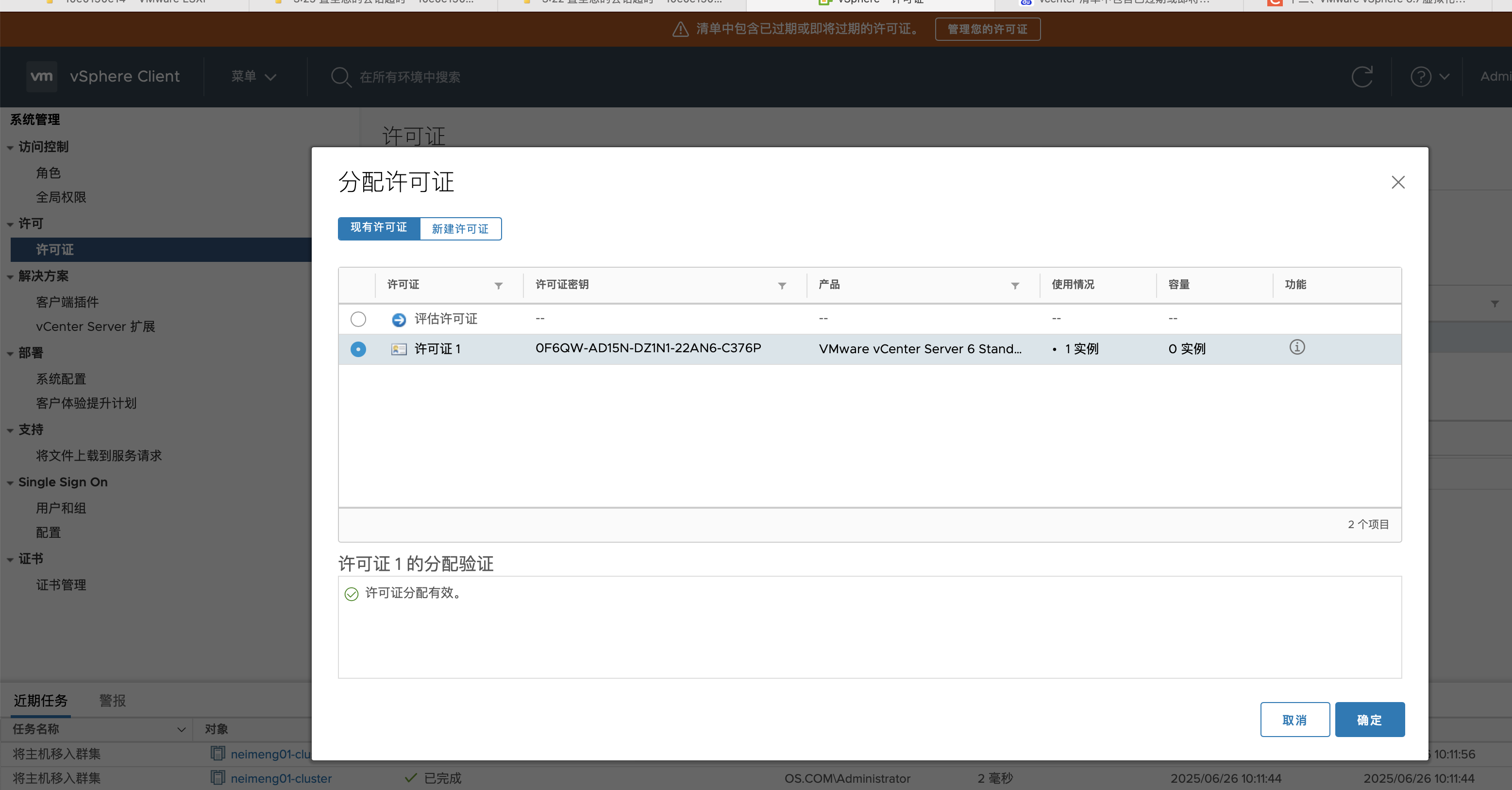
0F6QW-AD15N-DZ1N1-22AN6-C376P
esxi支持vsan许可证(企业版):0U0QJ-FR1EP-KZQN9-J1C74-23P5R
esxi支持vsan的许可证:NF4HH-F1K1Q-488R0-3L954-AF828
分配许可证¶
添加用户权限¶
https://jingyan.baidu.com/article/17bd8e527d1e5185ab2bb817.html
证书过期解决方法vc6.7¶
登录vcenter发现证书过期

解决方法如下:
登录vc所对应esxi,通过控制台开启vc的远程ssh服务

开启SSH服务

通过ssh服务远程连接vc
[root@localhost ~]# ssh 10.129.182.244
Warning: Permanently added '10.129.182.244' (ECDSA) to the list of known hosts.
VMware vCenter Server Appliance 6.7.0.41000
Type: vCenter Server with an embedded Platform Services Controller
root@10.129.182.244's password:
Connected to service
* List APIs: "help api list"
* List Plugins: "help pi list"
* Launch BASH: "shell"
Command>
输入shell进入vc root用户
Command> shell
Shell access is granted to root
root@10 [ ~ ]#
- 下载本文附带的fixsts.sh 脚本并将其上传到受影响的 PSC 或带有嵌入式 PSC 的 vCenter Server 的/tmp文件夹。
- 如果 SCP 客户端上传到 vCenter 的连接被拒绝,请从 SSH 会话运行此命令到 vCenter:chsh -s /bin/bash
- 如果您尚未按照第 2 步操作,请使用 SSH 会话连接到 PSC 或 vCenter Server。
- 导航到 /tmp 目录:
cd /tmp
脚本获取地址:https://kb.vmware.com/s/article/76719
脚本代码如下:
#!/bin/bash
# Copyright (c) 2020-2021 VMware, Inc. All rights reserved.
# VMware Confidential
#
# Run this from the affected PSC/VC
#
# NOTE: This works on external and embedded PSCs
# This script will do the following
# 1: Regenerate STS certificate
#
# What is needed?
# 1: Offline snapshots of VCs/PSCs
# 2: SSO Admin Password
NODETYPE=$(cat /etc/vmware/deployment.node.type)
if [ "$NODETYPE" = "management" ]; then
echo "Detected this node is a vCenter server with external PSC."
echo "Please run this script from a vCenter with embedded PSC, or an external PSC"
exit 1
fi
if [ "$NODETYPE" = "embedded" ] && [ ! -f /usr/lib/vmware-vmdir/sbin/vmdird ]; then
echo "Detected this node is a vCenter gateway"
echo "Please run this script from a vCenter with embedded PSC, or an external PSC"
exit 1
fi
echo "NOTE: This works on external and embedded PSCs"
echo "This script will do the following"
echo "1: Regenerate STS certificate"
echo "What is needed?"
echo "1: Offline snapshots of VCs/PSCs"
echo "2: SSO Admin Password"
echo "IMPORTANT: This script should only be run on a single PSC per SSO domain"
mkdir -p /tmp/vmware-fixsts
SCRIPTPATH="/tmp/vmware-fixsts"
LOGFILE="$SCRIPTPATH/fix_sts_cert.log"
echo "==================================" | tee -a $LOGFILE
echo "Resetting STS certificate for $HOSTNAME started on $(date)" | tee -a $LOGFILE
echo ""| tee -a $LOGFILE
echo ""
DN=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmdir]' | grep dcAccountDN | awk '{$1=$2=$3="";print $0}'|tr -d '"'|sed -e 's/^[ \t]*//')
echo "Detected DN: $DN" | tee -a $LOGFILE
PNID=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep PNID | awk '{print $4}'|tr -d '"')
echo "Detected PNID: $PNID" | tee -a $LOGFILE
PSC=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep DCName | awk '{print $4}'|tr -d '"')
echo "Detected PSC: $PSC" | tee -a $LOGFILE
DOMAIN=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep DomainName | awk '{print $4}'|tr -d '"')
echo "Detected SSO domain name: $DOMAIN" | tee -a $LOGFILE
SITE=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep SiteName | awk '{print $4}'|tr -d '"')
MACHINEID=$(/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost)
echo "Detected Machine ID: $MACHINEID" | tee -a $LOGFILE
IPADDRESS=$(ifconfig | grep eth0 -A1 | grep "inet addr" | awk -F ':' '{print $2}' | awk -F ' ' '{print $1}')
echo "Detected IP Address: $IPADDRESS" | tee -a $LOGFILE
DOMAINCN="dc=$(echo "$DOMAIN" | sed 's/\./,dc=/g')"
echo "Domain CN: $DOMAINCN"
ADMIN="cn=administrator,cn=users,$DOMAINCN"
USERNAME="administrator@${DOMAIN^^}"
ROOTCERTDATE=$(openssl x509 -in /var/lib/vmware/vmca/root.cer -text | grep "Not After" | awk -F ' ' '{print $7,$4,$5}')
TODAYSDATE=$(date | awk -F ' ' '{print $6,$2,$3}')
echo "#" > $SCRIPTPATH/certool.cfg
echo "# Template file for a CSR request" >> $SCRIPTPATH/certool.cfg
echo "#" >> certool.cfg
echo "# Country is needed and has to be 2 characters" >> $SCRIPTPATH/certool.cfg
echo "Country = DS" >> $SCRIPTPATH/certool.cfg
echo "Name = $PNID" >> $SCRIPTPATH/certool.cfg
echo "Organization = VMware" >> $SCRIPTPATH/certool.cfg
echo "OrgUnit = VMware" >> $SCRIPTPATH/certool.cfg
echo "State = VMware" >> $SCRIPTPATH/certool.cfg
echo "Locality = VMware" >> $SCRIPTPATH/certool.cfg
echo "IPAddress = $IPADDRESS" >> $SCRIPTPATH/certool.cfg
echo "Email = email@acme.com" >> $SCRIPTPATH/certool.cfg
echo "Hostname = $PNID" >> $SCRIPTPATH/certool.cfg
echo "==================================" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo ""
echo "Detected Root's certificate expiration date: $ROOTCERTDATE" | tee -a $LOGFILE
echo "Detected today's date: $TODAYSDATE" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
flag=0
if [[ $TODAYSDATE > $ROOTCERTDATE ]];
then
echo "IMPORTANT: Root certificate is expired, so it will be replaced" | tee -a $LOGFILE
flag=1
mkdir /certs && cd /certs
cp $SCRIPTPATH/certool.cfg /certs/vmca.cfg
/usr/lib/vmware-vmca/bin/certool --genselfcacert --outprivkey /certs/vmcacert.key --outcert /certs/vmcacert.crt --config /certs/vmca.cfg
/usr/lib/vmware-vmca/bin/certool --rootca --cert /certs/vmcacert.crt --privkey /certs/vmcacert.key
fi
echo "#" > $SCRIPTPATH/certool.cfg
echo "# Template file for a CSR request" >> $SCRIPTPATH/certool.cfg
echo "#" >> $SCRIPTPATH/certool.cfg
echo "# Country is needed and has to be 2 characters" >> $SCRIPTPATH/certool.cfg
echo "Country = DS" >> $SCRIPTPATH/certool.cfg
echo "Name = STS" >> $SCRIPTPATH/certool.cfg
echo "Organization = VMware" >> $SCRIPTPATH/certool.cfg
echo "OrgUnit = VMware" >> $SCRIPTPATH/certool.cfg
echo "State = VMware" >> $SCRIPTPATH/certool.cfg
echo "Locality = VMware" >> $SCRIPTPATH/certool.cfg
echo "IPAddress = $IPADDRESS" >> $SCRIPTPATH/certool.cfg
echo "Email = email@acme.com" >> $SCRIPTPATH/certool.cfg
echo "Hostname = $PNID" >> $SCRIPTPATH/certool.cfg
echo ""
echo "Exporting and generating STS certificate" | tee -a $LOGFILE
echo ""
cd $SCRIPTPATH
/usr/lib/vmware-vmca/bin/certool --server localhost --genkey --privkey=sts.key --pubkey=sts.pub
/usr/lib/vmware-vmca/bin/certool --gencert --cert=sts.cer --privkey=sts.key --config=$SCRIPTPATH/certool.cfg
openssl x509 -outform der -in sts.cer -out sts.der
CERTS=$(csplit -f root /var/lib/vmware/vmca/root.cer '/-----BEGIN CERTIFICATE-----/' '{*}' | wc -l)
openssl pkcs8 -topk8 -inform pem -outform der -in sts.key -out sts.key.der -nocrypt
i=1
until [ $i -eq $CERTS ]
do
openssl x509 -outform der -in root0$i -out vmca0$i.der
((i++))
done
echo ""
echo ""
read -s -p "Enter password for administrator@$DOMAIN: " DOMAINPASSWORD
echo ""
# Find the highest tenant credentials index
MAXCREDINDEX=1
while read -r line
do
INDEX=$(echo "$line" | tr -dc '0-9')
if [ $INDEX -gt $MAXCREDINDEX ]
then
MAXCREDINDEX=$INDEX
fi
done < <(/opt/likewise/bin/ldapsearch -h localhost -p 389 -b "cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "(objectclass=vmwSTSTenantCredential)" cn | grep cn:)
# Sequentially search for tenant credentials up to max index and delete if found
echo "Highest tenant credentials index : $MAXCREDINDEX" | tee -a $LOGFILE
i=1
if [ ! -z $MAXCREDINDEX ]
then
until [ $i -gt $MAXCREDINDEX ]
do
echo "Exporting tenant $i to $SCRIPTPATH" | tee -a $LOGFILE
echo ""
ldapsearch -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -b "cn=TenantCredential-$i,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > $SCRIPTPATH/tenantcredential-$i.ldif
if [ $? -eq 0 ]
then
echo "Deleting tenant $i" | tee -a $LOGFILE
ldapdelete -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "cn=TenantCredential-$i,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" | tee -a $LOGFILE
else
echo "Tenant $i not found" | tee -a $LOGFILE
echo ""
fi
((i++))
done
fi
echo ""
# Find the highest trusted cert chains index
MAXCERTCHAINSINDEX=1
while read -r line
do
INDEX=$(echo "$line" | tr -dc '0-9')
if [ $INDEX -gt $MAXCERTCHAINSINDEX ]
then
MAXCERTCHAINSINDEX=$INDEX
fi
done < <(/opt/likewise/bin/ldapsearch -h localhost -p 389 -b "cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "(objectclass=vmwSTSTenantTrustedCertificateChain)" cn | grep cn:)
# Sequentially search for trusted cert chains up to max index and delete if found
echo "Highest trusted cert chains index: $MAXCERTCHAINSINDEX" | tee -a $LOGFILE
i=1
if [ ! -z $MAXCERTCHAINSINDEX ]
then
until [ $i -gt $MAXCERTCHAINSINDEX ]
do
echo "Exporting trustedcertchain $i to $SCRIPTPATH" | tee -a $LOGFILE
echo ""
ldapsearch -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -b "cn=TrustedCertChain-$i,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > $SCRIPTPATH/trustedcertchain-$i.ldif
if [ $? -eq 0 ]
then
echo "Deleting trustedcertchain $i" | tee -a $LOGFILE
ldapdelete -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "cn=TrustedCertChain-$i,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" | tee -a $LOGFILE
else
echo "Trusted cert chain $i not found" | tee -a $LOGFILE
fi
echo ""
((i++))
done
fi
echo ""
i=1
echo "dn: cn=TenantCredential-1,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > sso-sts.ldif
echo "changetype: add" >> sso-sts.ldif
echo "objectClass: vmwSTSTenantCredential" >> sso-sts.ldif
echo "objectClass: top" >> sso-sts.ldif
echo "cn: TenantCredential-1" >> sso-sts.ldif
echo "userCertificate:< file:sts.der" >> sso-sts.ldif
until [ $i -eq $CERTS ]
do
echo "userCertificate:< file:vmca0$i.der" >> sso-sts.ldif
((i++))
done
echo "vmwSTSPrivateKey:< file:sts.key.der" >> sso-sts.ldif
echo "" >> sso-sts.ldif
echo "dn: cn=TrustedCertChain-1,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" >> sso-sts.ldif
echo "changetype: add" >> sso-sts.ldif
echo "objectClass: vmwSTSTenantTrustedCertificateChain" >> sso-sts.ldif
echo "objectClass: top" >> sso-sts.ldif
echo "cn: TrustedCertChain-1" >> sso-sts.ldif
echo "userCertificate:< file:sts.der" >> sso-sts.ldif
i=1
until [ $i -eq $CERTS ]
do
echo "userCertificate:< file:vmca0$i.der" >> sso-sts.ldif
((i++))
done
echo ""
echo "Applying newly generated STS certificate to SSO domain" | tee -a $LOGFILE
/opt/likewise/bin/ldapmodify -x -h localhost -p 389 -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -f sso-sts.ldif | tee -a $LOGFILE
echo ""
echo "Replacement finished - Please restart services on all vCenters and PSCs in your SSO domain" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo "IMPORTANT: In case you're using HLM (Hybrid Linked Mode) without a gateway, you would need to re-sync the certs from Cloud to On-Prem after following this procedure" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
if [ $flag == 1 ]
then
echo "Since your Root certificate was expired and was replaced, you will need to replace your MachineSSL and Solution User certificates" | tee -a $LOGFILE
echo "You can do so following this KB: https://kb.vmware.com/s/article/2097936" | tee -a $LOGFILE
fi
运行chmod +x fixsts.sh 使文件可执行。
chmod +x fixsts.sh
./fixsts.sh
使用以下命令重新启动 SSO 域中所有 vCenter 和/或 PSC 上的
service-control --stop --all
service-control --start --all
最后检查证书日期是否更新
root@10 [ /tmp ]# for i in $(/usr/lib/vmware-vmafd/bin/vecs-cli store list); do echo STORE $i; sudo /usr/lib/vmware-vmafd/bin/vecs-cli entry list --store $i --text | egrep "Alias|Not After"; done
STORE MACHINE_SSL_CERT
Alias : __MACHINE_CERT
Not After : Jul 2 08:44:55 2023 GMT
STORE TRUSTED_ROOTS
Alias : 2776de2dc14320f5b924d6f695c61e9a58473f51
Not After : Jun 18 09:11:51 2031 GMT
STORE TRUSTED_ROOT_CRLS
Alias : d8dd3ab559034022e8e80fb49449787f4fe7c71a
STORE machine
Alias : machine
Not After : Jun 18 09:11:51 2031 GMT
STORE vsphere-webclient
Alias : vsphere-webclient
Not After : Jun 18 09:11:51 2031 GMT
STORE vpxd
Alias : vpxd
Not After : Jun 18 09:11:51 2031 GMT
STORE vpxd-extension
Alias : vpxd-extension
Not After : Jun 18 09:11:51 2031 GMT
STORE APPLMGMT_PASSWORD
STORE data-encipherment
Alias : data-encipherment
Not After : Jun 18 09:11:51 2031 GMT
STORE SMS
Alias : sms_self_signed
Not After : Jun 23 09:15:10 2031 GMT
STORE BACKUP_STORE_H5C
Alias : bkp__MACHINE_CERT
Not After : Jul 2 08:44:45 2023 GMT
root@10 [ /tmp ]#
vsan故障¶
https://www.shangmayuan.com/a/f56b4524cd03409c9d52d145.html
vCenter Server 6.7 HTML 5客户端出现“没法提取请求的数据”的解决方法
在vCenter Server 6.7的HTML 5客户端中,在浏览“监控→vSAN→虚拟对象”时出现“没法提取请求的数据。请检查 vSphere Client 日志了解详细信息 (Failed to extract requested data. Check vSphere Client logs for details)。”,如图1所示。n

图1 错误1ssh
若是单击“主机”,在“监控→vSAN→性能”中也出相似的错误。ide
对于这个问题,VMware在KB74731(连接地址为https://kb.vmware.com/s/article/74731?lang=zh_CN)有介绍,而且说此问题在 ESXi 6.7 Update 3a 中已解决。但将ESXi与vCenter升级到Update 3a甚至更高版本以后,问题依旧。性能
这个环境中的vCenter Server 6.7是从6.5 U2升级而来。vCenter Server 6.5 U2有个bug,在证书到期而且续订了证书以后, vCenter Server没法登陆或提示密码不对,此时须要在https://kb.vmware.com/s/article/76719?lang=en_US&queryTerm=76719下载一个名为fixsts.sh脚本,上传到vCenter Server Appliance中执行该脚本,替换STS(Security Token Service)证书以解决密码不对问题。3d
在替换了STS证书以后,可能会致使计算机SSL证书与该vCenter Server节点URI所使用的服务注册所使用的SSL证书不匹配,就会出现图1的错误。对于这个问题,能够使用check-trust-anchors -cml脚本修复。日志
使用ssh登陆到vCenter Server,在/tmp文件夹中使用vi check-trust-anchors编辑新的文件,而后在Windows计算机上,用“记事本”打开下载的check-trust-anchors文件,复制全部内容,在vi中按一下insert按钮,粘贴复制的内容,按一下ESC键,输入:wq保存退出。对象
代码获取地址:https://web.vmware-labs.com/scripts/check-trust-anchors
代码如下:
#!/bin/bash
#------------------------------
# Script to check and fix SSL trust achors
#
# Author: Vincent Santa Maria [vsantamaria@vmware.com]
# Version: 2.1
#------------------------------
function setOptionColorize() {
RED=$(tput setaf 1)
GREEN=$(tput setaf 2)
YELLOW=$(tput setaf 3)
CYAN=$(tput setaf 6)
NORMAL=$(tput sgr0)
}
function unknownOption() {
echo "Unknown option '$2'. Please see '$1 --help' for usage and available options"
}
CURRENT_SERVICE_ID=''
SHOW_SERVICE_IDS=0
SHOW_ENDPOINTS=0
SHOW_DUPLICATE_ENDPOINTS=0
LIVE_CHECK=0
VIEW_MACHINE_SSL=0
DEBUG=0
FIX=0
TP_ALGORITHM="sha1"
TP_REGEX_ITER="19"
CERT_TEXT=0
CERT_COUNT=1
RED=''
GREEN=''
YELLOW=''
CYAN=''
NORMAL=''
LSTOOL_FILE='lstool.txt'
if [[ ${LIVE_CHECK} -gt 0 ]]; then
VC_VERSION=$(grep 'CLOUDVM_VERSION:' /etc/vmware/.buildInfo | awk -F':' '{print $NF}' | awk -F'.' '{print $1}')
else
VC_VERSION=$(grep 'CLOUDVM_VERSION:' ../etc/vmware/.buildInfo | awk -F':' '{print $NF}' | awk -F'.' '{print $1}')
fi
if [[ ${VC_VERSION} -eq 7 ]]; then
LS_PORT='7090'
LSTOOL_SCRIPT='/usr/lib/vmware-lookupsvc/tools/lstool.py'
LSUPDATE_SCRIPT='/usr/lib/vmware-lookupsvc/tools/ls_update_certs.py'
else
LS_PORT='7080'
LSTOOL_SCRIPT='/usr/lib/vmidentity/tools/scripts/lstool.py'
LSUPDATE_SCRIPT='/usr/lib/vmidentity/tools/scripts/ls_update_certs.py'
fi
if [ -f /usr/bin/ldapsearch ]; then
LDAPSEARCH='/usr/bin/ldapsearch'
else
LDAPSEARCH='/opt/likewise/bin/ldapsearch'
fi
if [ "$#" -ge 1 ]; then
for arg in "$@"; do
case ${arg} in
-h|--help)
echo "SSL Trust Anchor Verification and Remediation Script"
echo "Usage: $0 [options]"
echo "Options:"
echo " -s | --show-service-ids Shows the Service IDs that are using a particular SSL certificate."
echo " -e | --show-endpoints Shows the Endpoing URIs that are using a particular SSL certificate."
echo " -c | --colorize Colorizes text for quick identification of Subject field, SHA1/SHA256 Fingerprint, or"
echo " expired certificates. Do not use if passing output to a paginator or file."
echo " -l | --live-check Used when running the script on a live system, which will automatically dump the"
echo " Lookup Service registrations to /tmp. Must be used with the fix (-f|--fix) option."
echo " -m | --machine-ssl Will display information on the current Machine SSL ceritifcate. Cannot be run on"
echo " a support bundle from an external Platform Services Controller."
echo " -t | --cert-text Will provide full output of each certificate similar to 'openssl x509 -text'"
echo " -f | --fix Will prompt for SSO credentials, thumbprint of a trust anchor cert to update, and the IP/FQDN"
echo " of a node to update."
echo " -d | --debug Will include the raw certificate hash to see if there are any extra characters"
echo " (sometimes the lstool.py script has connection issues and STDERR gets randomly"
echo " inserted in the output)."
echo " -h | --help Prints this help menu."
echo " -2 | --sha256 Outputs the SHA256 thumbprint of the certificates instead of the SHA1 thumbprint"
echo $'\n'"Parses the output of the following command from the Platform Services Controller:"
echo "${LSTOOL_SCRIPT} list --url http://localhost:${LS_PORT}/lookupservice/sdk 2>/dev/null"
echo $'\n'"Can be run from the 'commands/' directory of a support bundle, or live on a PSC node."
exit
;;
--show-service-ids)
SHOW_SERVICE_IDS=1
;;
--show-endpoints)
SHOW_ENDPOINTS=1
;;
--colorize)
setOptionColorize
;;
--live-check)
LIVE_CHECK=1
;;
--machine-ssl)
VIEW_MACHINE_SSL=1
;;
--debug)
DEBUG=1
;;
--cert-text)
CERT_TEXT=1
;;
--fix)
FIX=1
;;
--sha256)
TP_ALGORITHM="sha256"
TP_REGEX_ITER="31"
;;
-[seclmfdt2]*)
OPT=$(echo "z${arg}" | sed 's/z-//')
for (( i=0; i<${#OPT}; i++ )); do
case ${OPT:$i:1} in
s)
SHOW_SERVICE_IDS=1
;;
e)
SHOW_ENDPOINTS=1
;;
c)
setOptionColorize
;;
d)
DEBUG=1
;;
l)
LIVE_CHECK=1
;;
m)
VIEW_MACHINE_SSL=1
;;
t)
CERT_TEXT=1
;;
f)
FIX=1
;;
2)
TP_ALGORITHM="sha256"
TP_REGEX_ITER="31"
;;
*)
unknownOption $0 '-${OPT:$i:1}'
exit
;;
esac
done
;;
*)
unknownOption $0 ${arg}
exit
;;
esac
done
fi
if [[ ${LIVE_CHECK} -eq 0 ]]; then
if [ ! -f ${LSTOOL_FILE} ]; then
if [ ! -f "python.exe_VMWARE_CIS_HOMEVMwareIdentityServiceslstoolscriptslstoolpy-list---url-httplocalhost7080lo[...].txt" ]; then
echo "${YELLOW}No output from 'lstool.py list' found in this bundle."
else
LSTOOL_FILE='python.exe_VMWARE_CIS_HOMEVMwareIdentityServiceslstoolscriptslstoolpy-list---url-httplocalhost7080lo[...].txt'
fi
fi
if [ -f ../etc/vmware/deployment.node.type ]; then
NODE_TYPE=$(cat ../etc/vmware/deployment.node.type)
elif [ -f ../ProgramData/VMware/vCenterServer/cfg/deployment.node.type ]; then
NODE_TYPE=$(cat ../ProgramData/VMware/vCenterServer/cfg/deployment.node.type)
fi
else
NODE_TYPE=$(cat /etc/vmware/deployment.node.type)
if [ ${NODE_TYPE} == 'management' ]; then
echo "${YELLOW}Operation not supported on a Management Node. Please run this live on a PSC node. Exiting...${NORMAL}"
exit
fi
if [ ! -f ${LSTOOL_FILE} ]; then LSTOOL_FILE='/tmp/lstool.txt'; fi
echo "${YELLOW}No 'lstool.txt' file found in this directory. Dumping service registrations to ${LSTOOL_FILE}...${NORMAL}"
${LSTOOL_SCRIPT} list --url http://localhost:${LS_PORT}/lookupservice/sdk 2>/tmp/lstool_stderr > ${LSTOOL_FILE}
fi
DATA=$(cat ${LSTOOL_FILE} | grep -vE '^[0-9]{4}-[0-9]{2}-[0-9]{2}' | grep -E 'Service ID:|URL:|SSL trust:|^[0-9A-Za-z/\+]' | tr -d ' ' | tr -d '\n' | tr -d '\t' | tr -d '\r\n' | sed -e 's/ServiceID:/\nServiceID:/g' -e 's/URL:/\nURL:/g' -e 's/SSLtrust:/\nSSLtrust:/g')
TRUST_ANCHORS=$(echo "${DATA}" | grep 'SSLtrust' | sed -e 's/SSLtrust://g' | sort | uniq)
for RAW_HASH in ${TRUST_ANCHORS}; do
echo "${CYAN}-----Endpoint Certificate ${CERT_COUNT}-----${NORMAL}"
if [[ ${RAW_HASH} =~ [0-9]{4}-[0-9]{2}-[0-9]{2} ]]; then
echo "${RED}Malformed hash detected${NORMAL}"
BAD=$(echo "${RAW_HASH}" | grep -oE '[0-9]{4}-[0-9]{2}-[0-9]{2}(.)+')
HASH="$(echo "${RAW_HASH}" | sed -e 's/${BAD}//')"
CHARS=${#HASH}
MOD=$((${CHARS} % 4))
case ${MOD} in
3)
HASH="${HASH}="
;;
2)
HASH="${HASH}=="
;;
esac
else
HASH=${RAW_HASH}
fi
CURRENT_CERT="-----BEGIN CERTIFICATE-----"$'\n'
CURRENT_CERT+=$(echo ${HASH} | fold -c64)
CURRENT_CERT+=$'\n'"-----END CERTIFICATE-----"
if echo "${CURRENT_CERT}" | openssl x509 -text > /dev/null 2>&1; then
if [[ ${CERT_TEXT} -gt 0 ]]; then
CURRENT_CERT_INFO=$(echo "${CURRENT_CERT}" | openssl x509 -text -noout -fingerprint -${TP_ALGORITHM} | sed -e 's/SHA[0-9]* Fingerprint/\t&/g' -e "s/Subject:/${GREEN}&${NORMAL}/g" -e "s/[[:xdigit:]]\{2\}\(:[[:xdigit:]]\{2\}\)\{${TP_REGEX_ITER}\}/${YELLOW}&${NORMAL}/g" -e "s/X509v3 Subject Alternative Name/${GREEN}&${NORMAL}/g")
echo "${CURRENT_CERT_INFO}"
else
CURRENT_CERT_INFO=$(echo "${CURRENT_CERT}" | openssl x509 -text -noout -fingerprint -${TP_ALGORITHM} | grep -E 'Issuer:|Subject:|Validity|Not Before:|Not After :|Fingerprint' | sed -e 's/SHA[0-9]* Fingerprint/\t&/g' -e "s/Subject:/${GREEN}&${NORMAL}/g" -e "s/[[:xdigit:]]\{2\}\(:[[:xdigit:]]\{2\}\)\{${TP_REGEX_ITER}\}/${YELLOW}&${NORMAL}/g")
echo "Certificate Info:"
if echo "${CURRENT_CERT}" | openssl x509 -noout -checkend 0; then
echo "${CURRENT_CERT_INFO}"
else
echo "${CURRENT_CERT_INFO}" | sed -e "s/Not Before/${RED}&/"
fi
if [[ ${DEBUG} -gt 0 ]]; then echo $'\t'"Certificate Hash: ${HASH}"; fi
fi
else
echo "${RED}Unable to parse certificate hash${NORMAL}"
if [[ ${DEBUG} -gt 0 ]]; then echo "${HASH}"; fi
fi
if [[ ${SHOW_SERVICE_IDS} -gt 0 ]]; then
REGEX_HASH=$(echo "${RAW_HASH}" | sed -e 's/\+/\\+/g' -e 's/\$/\\$/g')
FOUND_SERVICE_IDS=''
for line in $(echo "${DATA}" | grep -vE '^URL:' | uniq | grep -E "ServiceID|${REGEX_HASH}" | grep -B1 ${RAW_HASH}); do
if [[ "${line}" =~ ^ServiceID ]]; then
CURRENT_SERVICE_ID=$(echo "${line}" | sed -e 's/ServiceID://g')
elif $(echo "${line}" | grep ${RAW_HASH} > /dev/null); then
if [ -z "${FOUND_SERVICE_IDS}" ]; then
FOUND_SERVICE_IDS=$'\t'"${CURRENT_SERVICE_ID}"
else
FOUND_SERVICE_IDS+=$'\n\t'"${CURRENT_SERVICE_ID}"
fi
fi
done
NUM_FOUND_SERVICE_IDS=$(echo "${FOUND_SERVICE_IDS}" | sort | uniq | wc -l)
echo "Service IDs (${NUM_FOUND_SERVICE_IDS}):"
echo "${FOUND_SERVICE_IDS}" | sort | uniq
fi
if [[ ${SHOW_ENDPOINTS} -gt 0 ]]; then
ENDPOINTS=$(echo "${DATA}" | grep -vE '^ServiceID' | grep -B1 ${RAW_HASH} | grep -E '^URL:' | sed -e 's/URL:/\t/g' | sort | uniq)
NUM_ENDPOINTS=$(echo "${ENDPOINTS}" | wc -l)
echo "Endpoints (${NUM_ENDPOINTS}):"
echo "${ENDPOINTS}"
fi
echo "${CYAN}--------------------------------${NORMAL}"
((++CERT_COUNT))
done
if [[ ${VIEW_MACHINE_SSL} -gt 0 ]]; then
if [[ ${LIVE_CHECK} -eq 0 ]]; then
if [ "${NODE_TYPE}" = 'infrastructure' ]; then
echo $'\n'"${YELLOW}The Machine SSL certificate is not included in an external PSC support bundle.${NORMAL}"
else
if [ -f ../etc/vmware-vpx/ssl/rui.crt ]; then
MACHINE_SSL_FILE='../etc/vmware-vpx/ssl/rui.crt'
elif [ -f ../ProgramData/VMware/vCenterServer/cfg/vmware-vpx/ssl/rui.crt ]; then
MACHINE_SSL_FILE='../ProgramData/VMware/vCenterServer/cfg/vmware-vpx/ssl/rui.crt'
fi
if [ ! -z ${MACHINE_SSL_FILE} ]; then
echo $'\n'"${CYAN}-----Machine SSL Certificate-----${NORMAL}"
CURRENT_MACHINE_SSL_CERT_INFO=$(cat ${MACHINE_SSL_FILE} | openssl x509 -text -noout -fingerprint -${TP_ALGORITHM} | grep -E 'Issuer:|Subject:|Validity|Not Before:|Not After :|Fingerprint' | sed -e 's/SHA[0-9]* Fingerprint/\t&/g' -e "s/Subject:/${GREEN}&${NORMAL}/g" -e "s/[[:xdigit:]]\{2\}\(:[[:xdigit:]]\{2\}\)\{${TP_REGEX_ITER}\}/${YELLOW}&${NORMAL}/g")
echo "Certificate Info:"
if cat "${MACHINE_SSL_FILE}" | openssl x509 -noout -checkend 0; then
echo "${CURRENT_MACHINE_SSL_CERT_INFO}"
else
echo "${CURRENT_MACHINE_SSL_CERT_INFO}" | sed -e "s/Not Before/${RED}&/"
fi
echo "${CYAN}---------------------------------${NORMAL}"
else
echo $'\n'"${YELLOW}Unable to locate the Machine SSL certificate file in the support bundle.${NORMAL}"
fi
fi
else
SSO_DOMAIN=$(/usr/lib/vmware-vmafd/bin/vmafd-cli get-domain-name --server-name localhost)
SSO_SITE=$(/usr/lib/vmware-vmafd/bin/vmafd-cli get-site-name --server-name localhost)
VMDIR_DC_BRANCH="dc=$(echo ${SSO_DOMAIN} | sed 's/\./,dc=/g')"
VMDIR_MACHINE_PASSWORD=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\services\vmdir]' | grep dcAccountPassword | awk -F" " '{print $NF}' | awk '{print substr($0,2,length($0)-2)}' | sed -e 's/\\"/"/g' -e 's/\\\\/\\/g' | tr -d '\n' > /tmp/.vmdir_machine_account_password; chmod go-r /tmp/.vmdir_machine_account_password)
VMDIR_MACHINE_ACCOUNT_DN=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\services\vmdir]' | grep '"dcAccountDN"' | awk -F" " '{print $NF}' | awk '{print substr($0,2,length($0)-2)}')
SSO_NODES=()
PSC_NODES=$($LDAPSEARCH -LLL -h localhost -p 389 -b "ou=Domain Controllers,$VMDIR_DC_BRANCH" -D "$VMDIR_MACHINE_ACCOUNT_DN" -y /tmp/.vmdir_machine_account_password "(objectclass=computer)" cn | grep '^cn:' | awk '{print $2}')
PSC_COUNT=$(echo "${PSC_NODES}" | wc -l)
VCENTER_NODES=$($LDAPSEARCH -LLL -h localhost -p 389 -b "ou=Computers,$VMDIR_DC_BRANCH" -D "$VMDIR_MACHINE_ACCOUNT_DN" -y /tmp/.vmdir_machine_account_password "(objectclass=computer)" cn | grep '^cn:' | awk '{print $2}')
VCENTER_COUNT=$(echo "${VCENTER_NODES}" | wc -l)
for psc_node in "$PSC_NODES"; do
if [[ ! "${SSO_NODES[@]}" =~ "$psc_node" ]]; then SSO_NODES+=($psc_node); fi
done
for vc_node in "$VCENTER_NODES"; do
if [[ ! "${SSO_NODES[@]}" =~ "$vc_node" ]]; then SSO_NODES+=($vc_node); fi
done
rm /tmp/.vmdir_machine_account_password
printf '\n'
for node in "${SSO_NODES[@]}"; do
echo "${CYAN}-----Machine SSL Certificate-----${NORMAL}"
echo "${CYAN}${node}${NORMAL}"
CURRENT_MACHINE_SSL_CERT_INFO=$(echo | openssl s_client -connect ${node}:443 2>/dev/null | openssl x509 -text -noout -fingerprint -${TP_ALGORITHM} 2>/dev/null | grep -E 'Issuer:|Subject:|Validity|Not Before:|Not After :|Fingerprint' | sed -e 's/SHA[0-9]* Fingerprint/\t&/g' -e "s/Subject:/${GREEN}&${NORMAL}/g" -e "s/[[:xdigit:]]\{2\}\(:[[:xdigit:]]\{2\}\)\{${TP_REGEX_ITER}\}/${YELLOW}&${NORMAL}/g")
echo "Certificate Info:"
if [ "$CURRENT_MACHINE_SSL_CERT_INFO" != "" ]; then
if echo | openssl s_client -connect ${node}:443 2>/dev/null | openssl x509 -noout -checkend 0; then
echo "${CURRENT_MACHINE_SSL_CERT_INFO}"
else
echo "${CURRENT_MACHINE_SSL_CERT_INFO}" | sed -e "s/Not Before/${RED}&/"
fi
else
echo $'\t'"${YELLOW}Unable to retrieve certificate information from ${node}${NORMLA}"
fi
echo "${CYAN}---------------------------------${NORMAL}"
done
fi
fi
if [[ ${FIX} -gt 0 ]]; then
if [[ ${LIVE_CHECK} -gt 0 ]]; then
if [ ! -f ${LSUPDATE_SCRIPT} ]; then
echo $'\n'"${YELLOW}The ${LSUPDATE_SCRIPT} script could not be found. Please ensure you are running this from a PSC.${NORMAL}"
else
echo $'\n'"${CYAN}SSL Trust Anchor Repair${NORMAL}"
echo "${CYAN}---------------------------------${NORMAL}"
echo "This process will attempt to update the SSL trust anchors for Lookup Service registrations using native Lookup Service libraries. These changes should propagate to all PSCs in the SSO domain."
echo $'\n'"${YELLOW}It is strongly recommended that you take offline snapshots of all PSCs in the SSO domain before proceeding.${NORMAL}"
read -p $'\n'"Proceed with updating trust anchors? [Y/N]: " PROCEED
if [ -z ${PROCEED} ]; then PROCEED_FIX="n"; else PROCEED_FIX=$(echo ${PROCEED} | awk '{print tolower(substr($0,0,1))}'); fi
if [ ${PROCEED_FIX} == "y" ]; then
SSO_DOMAIN=$(/usr/lib/vmware-vmafd/bin/vmafd-cli get-domain-name --server-name localhost)
read -p $'\n'"Enter SSO admin [administrator@${SSO_DOMAIN}]: " LOGIN
if [ -z ${LOGIN} ]; then LOGIN="administrator@${SSO_DOMAIN}"; fi
read -s -p "Enter password for ${LOGIN}: " PASSWORD_INPUT
PASSWORD=$(echo ${PASSWORD_INPUT} | sed "s/'/'\\\''/g")
read -p $'\n'"Enter fingerprint of trust anchor(s) to update: " FINGERPRINT
read -p "Enter the FQDN of the node to update: " NODE_FQDN
if echo 'y' | openssl s_client -connect ${NODE_FQDN}:443 2>/dev/null | openssl x509 > /tmp/machine-ssl.crt; then
if ! ${LSUPDATE_SCRIPT} --url http://localhost:${LS_PORT}/lookupservice/sdk 2>/tmp/ls_update_certs.stderr --fingerprint ${FINGERPRINT} --certfile /tmp/machine-ssl.crt --user ${LOGIN} --password $(eval echo "'${PASSWORD}'"); then
echo $'\n'"${YELLOW}The ls_update_certs.py script encountered an error."
echo $'\n'"Please refer to /tmp/ls_update_certs.stderr for more information.${NORMAL}"
fi
else
echo $'\n'"${YELLOW}Unable to obtain SSL certificate from ${NODE_FQDN}. Exiting..."
fi
else
echo $'\n'"Operation aborted. Exiting..."
fi
fi
else
echo $'\n'"${YELLOW}Fixing trust anchors can only be done on a live system.${NORMAL}"
fi
fi
而后执行
chmode +x check-trust-anchorsblog
./ check-trust-anchors -cmlf
修复证书。get

图2 修复SSL证书
查看SHA1 Fingerprint=后面的字符串,能够看到有一条指纹不匹配,此示例为B9:77:05:11:00:88:72:B1:E5:CC:18:42:8E:39:01:D6:E2:B7:91:94
在如下输入Y、SSO账户、密码,输入要更新的信任锚的指纹
Proceed with updating trust anchors? [Y/N]: y
Enter SSO admin [administrator@vsphere.local]: administrator@vsphere.local
Enter password for administrator@vsphere.local:
Enter fingerprint of trust anchor(s) to update: B9:77:05:11:00:88:72:B1:E5:CC:18:42:8E:39:01:D6:E2:B7:91:94
Enter the FQDN of the node to update: VC名字或IP
更新完成后问题便可解决,如图3所示。

vcenter忘记密码¶
VCSA底层root密码忘记